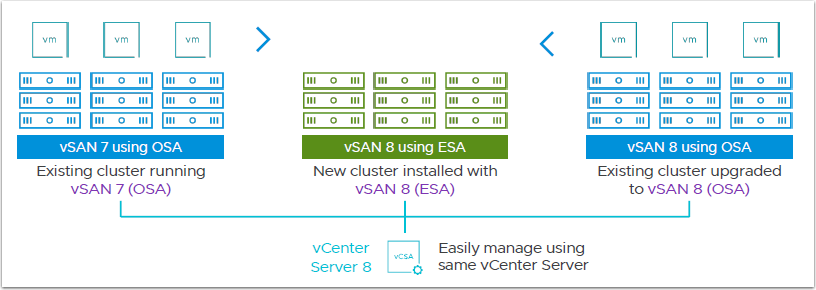
VMware vSAN ESA was actually launched in vSAN 8 back in late 2022, you can read some details here.
Now with the addition of the Amazon i41 Metal instance type, vSAN ESA will be available in the VMware Cloud on AWS.
The i4i metal instance will be the only supported hardware to deploy a vSAN ESA Cluster on your VMC on AWS SDDC. However all cluster types will be supported-
Now with the addition of the Amazon i41 Metal instance type, vSAN ESA will be available in the VMware Cloud on AWS.
The i4i metal instance will be the only supported hardware to deploy a vSAN ESA Cluster on your VMC on AWS SDDC. However all cluster types will be supported-
Since vSAN 8 ESA has been out for some time, there are a number of articles and blogs that go into the new architecture and features.
Some of the more interesting new features are:
-Lower CPU usage per IO
-ESA does not have Disk Groups, all the hosts disks will be added to a Storage Pool, and all disks provide capacity and performance. There is no dedicated caching disks.
-RAID-5 and RAID-6 at the performance of RAID-1
-Compression enabled by default, and 4x increased compression
-Component count per host limit is increased from 9,000 components to 27,000 components
-support for 25GB network adapters
-Improved snapshot performance
-Data at Rest Encryption enabled
-Updated Skyline Health, based on the cluster health score
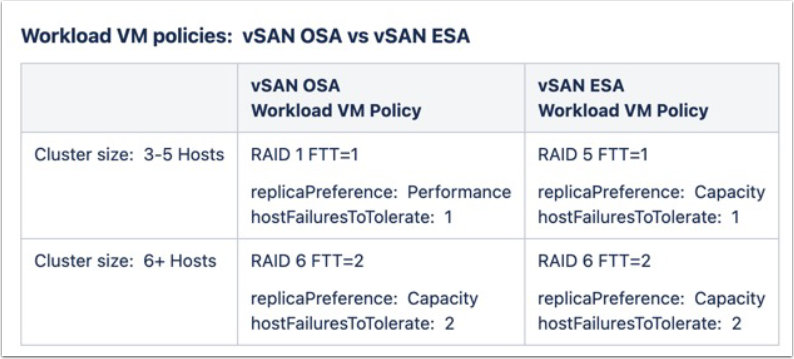
-For VMC on AWS SDDC's, different Storage Policies:
• 3-5 nodes uses RAID5/FTT = 1 for management and workload
• 6+ nodes uses RAID6/FTT = 2
For more details on the new features and architecture, check out the FAQ Page
Some of the more interesting new features are:
-Lower CPU usage per IO
-ESA does not have Disk Groups, all the hosts disks will be added to a Storage Pool, and all disks provide capacity and performance. There is no dedicated caching disks.
-RAID-5 and RAID-6 at the performance of RAID-1
-Compression enabled by default, and 4x increased compression
-Component count per host limit is increased from 9,000 components to 27,000 components
-support for 25GB network adapters
-Improved snapshot performance
-Data at Rest Encryption enabled
-Updated Skyline Health, based on the cluster health score
-For VMC on AWS SDDC's, different Storage Policies:
• 3-5 nodes uses RAID5/FTT = 1 for management and workload
• 6+ nodes uses RAID6/FTT = 2
For more details on the new features and architecture, check out the FAQ Page
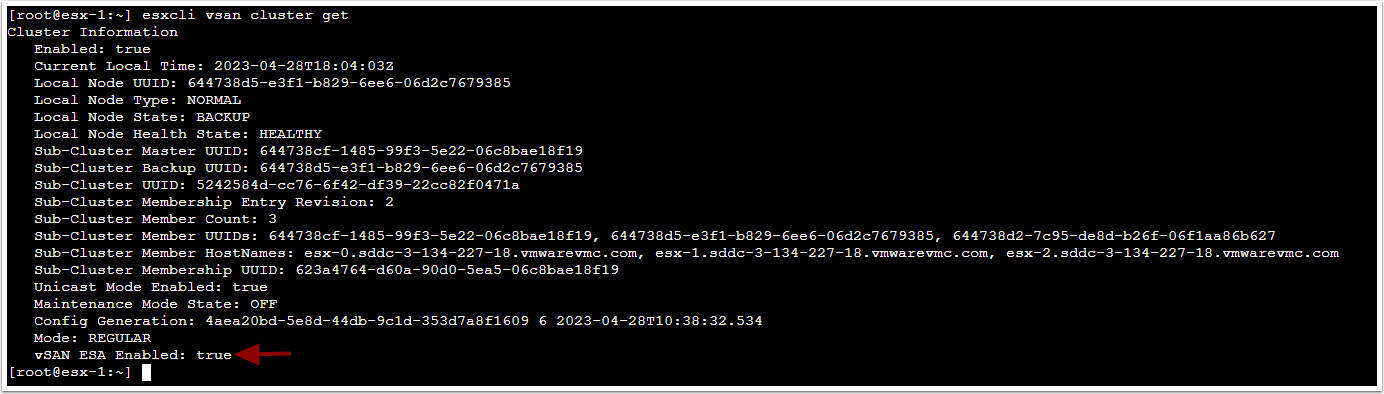
As shown above, when running the esxcli vsan cluster get command on a host, it will show the vSAN ESA Enabled: True
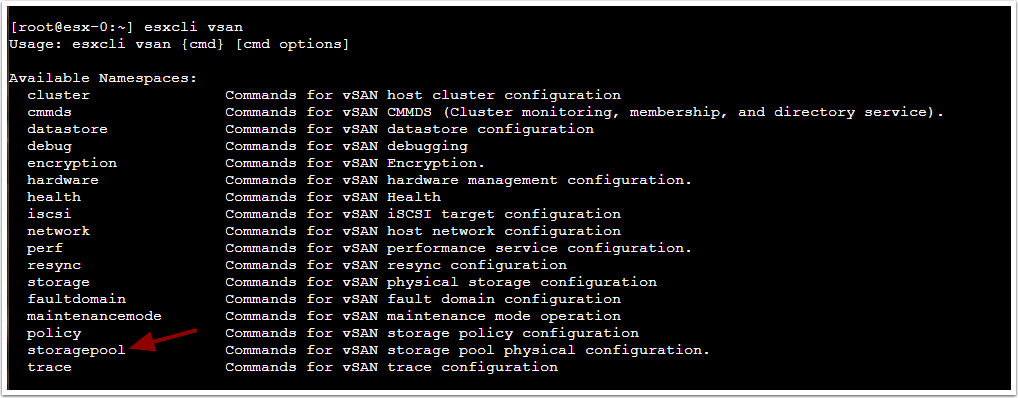
Shown above, the esxcli vsan command lists the option to display the Storage Pool.
For VMC on AWS SDDC Clusters, the new Storage Policies can now provide RAID-5 FTT=1 on a 3 host cluster:
For VMC on AWS SDDC Clusters, the new Storage Policies can now provide RAID-5 FTT=1 on a 3 host cluster:
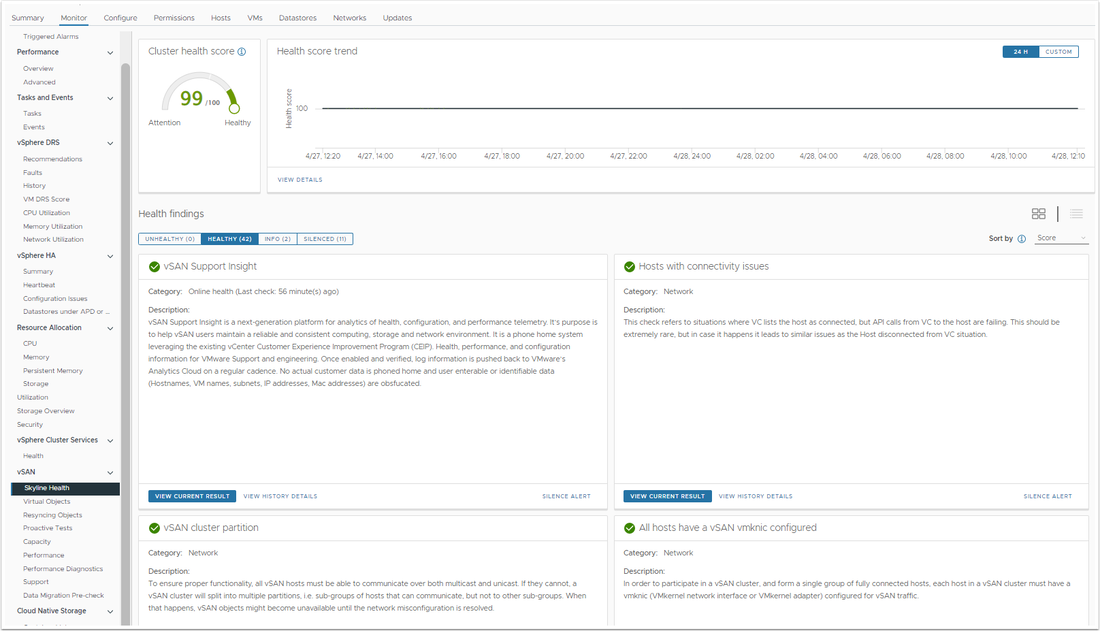
Skyline Health shows health score for the cluster, which allows you to view past health scores and select the details from the Health Findings:
I am currently testing vSAN ESA for the VMC on AWS rollout, and I will add more details when it is released.
For more info you can watch the Virtually Speaking Podcast on vSAN 8 ESA.
Enjoy!!
For more info you can watch the Virtually Speaking Podcast on vSAN 8 ESA.
Enjoy!!






 RSS Feed
RSS Feed