What does the giant cat picture above have to do with this? Absolutely nothing! In my free time I volunteering at a local cat sanctuary, and we are always posting silly cat pictures...Sorry....
Anyway, back to the vTPM topic.
When you have the requirements set up, and your ESXi hosts are now in Encryption Mode, that means any core dumps and the vm-support files will be encrypted.
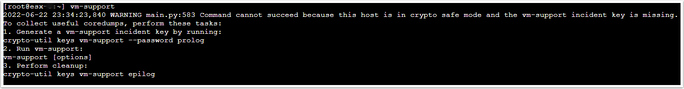
So on an ESXi host with encryption enabled you will get this when you run the log bundle collection with the vm-support command:
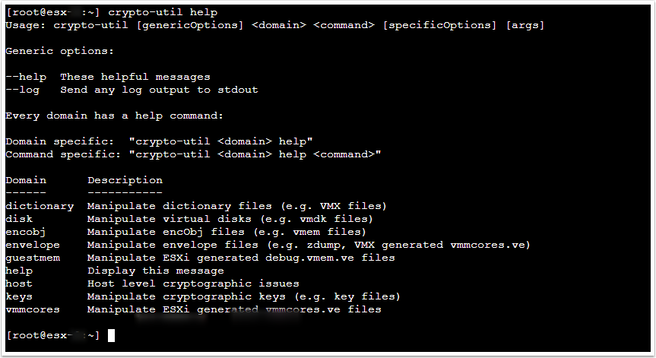
The VMware articles use the crypto-util utility.
Crypto-util can be launched from the root of an ESXi server, and is in /bin/crypto-util
will appear at the top of the host support bundle. The vm-support-incident-key file contains a the incident key which is dynamically generated each time vm-support runs, and crypto-util vm-support prolog is run before it. The incident key is encrypted/wrapped via the specified password.
Some details on the core dump files-
All encrypted core dump files include the key ID (keyID) of the key required for decryption. The keyID can be used to locate a key and its attributes from a Key Management Server (KMS), from the ESXi key cache, or from a key file.
zdump files:
- Unencrypted zdump files are the same as they always have been - A zdump header followed by data
- Encrypted zdump files contain a zdump header (with minimal information including that the core dump is encrypted), followed by an envelope header, and there the encrypted data begins. The encrypted data contains the "real" zdump header and data
- vmkdump_extract will recognize an encrypted zdump but is unable to manipulate it. It will, however, advise you as to how to decrypted the zdump
- Unencrypted monitor core dumps are placed in vmmcores.gz - a monitor core dump file that is compressed
- Encrypted monitor core dumps are placed in vmmcores.ve - a monitor core dump file which has been compressed and encrypted
If you ever run into this I sure hope this will be helpful!


 RSS Feed
RSS Feed